One-Hour AD Compromise
Fill the form to download our latest sample penetration testing report
Explore Related Resource
Methodologies & Case studies

One-Hour AD Compromise
Case Study

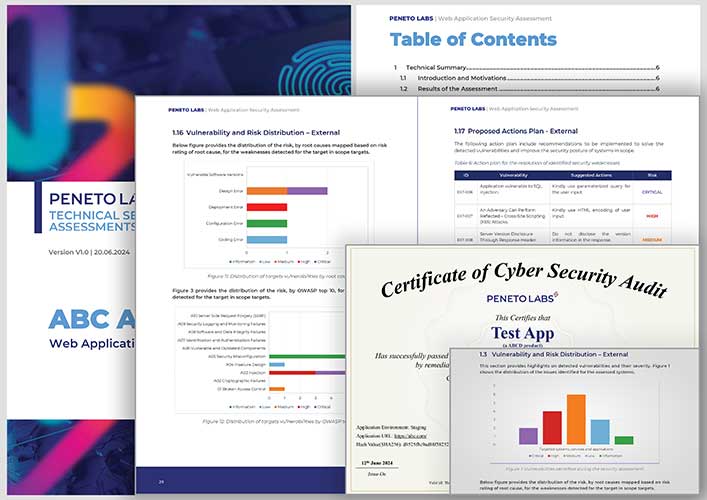
Web Application Penetration Testing
Methodology

Network Penetration Testing
Methodology

Mobile Application Penetration Testing
Methodology

Vulnerability Assessment Penetration Testing
Methodology

API Penetration Testing
Methodology
Why to Choose Peneto Labs Expert Penetration Testing Services
Prevent Breaches and stay compliant

Certified Experts
Our consultants hold cyber security certifications such as SANS/GIAC GXPN, GAWN, GPEN, GWAPT, GRID, GCIH, OSCE, OSWP, OSCP, CEH, CREST etc.This means your hiring WORLD CLASS SECURITY EXPERTS to fight against Hackers trying to attack your infrastructure.

International Best Practices
We carry out each assessment by following international standards and testing methodologies, such as OWASP, NIST, and PTES, along with our unique and specific threat modellings to attain highest quality results.

Well Documented Reports
Our report insights that are remediative and decisive to make your information security risk management program successful. We strive to provide more HELPFUL information instead of just MORE information.

Cert-In Empanelled IT Security Auditor
High credibility is always inherent when obtaining your audit certification from Peneto Labs. This organisation is empanelled by CERT-In to provide information Security Auditing Services.

Certified Experts
Our consultants hold cyber security certifications such as SANS/GIAC GXPN, GAWN, GPEN, GWAPT, GRID, GCIH, OSCE, OSWP, OSCP, CEH, CREST etc.This means your hiring WORLD CLASS SECURITY EXPERTS to fight against Hackers trying to attack your infrastructure.

International Best Practices
We carry out each assessment by following international standards and testing methodologies, such as OWASP, NIST, and PTES, along with our unique and specific threat modellings to attain highest quality results.

Well Documented Reports
Our report insights that are remediative and decisive to make your information security risk management program successful. We strive to provide more HELPFUL information instead of just MORE information.

Cert-In Empanelled IT Security Auditor
High credibility is always inherent when obtaining your audit certification from Peneto Labs. This organisation is empanelled by CERT-In to provide information Security Auditing Services.
Tell Us About Your Challenges
We’ll Talk to You the Same Business Day
What happens next
- We reach out to understand your current challenges and align with your vision and business compliance requirements.
- We collaborate to define your project’s scope.
- You receive a no-obligation proposal.

WhatsApp us