Automated vs Manual Penetration Testing for Web Apps: Which is Right for You?

Be it automated penetration testing or manual penetration testing, each approach has benefits and drawbacks. This scenario certainly creates a significant challenge for organizations striving to enhance security. While automated penetration testing offers efficiency, manual penetration testing gives applications a human touch and adaptability.
After undergoing many scans, we have seen that automated penetration testing alone is insufficient for a thorough check. These tools are generally programmed to identify common flaws by following a set pattern. However, as the industry evolves, modern applications are more than just a common configuration that automated tools fail to comprehend fully.
Not only common vulnerabilities, automated scans often miss zero-day vulnerabilities and complex security flaws. Further, automated scans often rely on vulnerability databases through which they miss unknown threats.
Automated tools are also highly likely to generate false negatives and positives. False positives happen when automated tools identify vulnerabilities incorrectly. As for false negatives, tools fail to identify genuine vulnerabilities, leaving the application with potential risks.
What is Penetration Testing?
The primary goals of penetration testing are as follows:
- Identifying vulnerabilities that could be exploited.
- Improving security and offering actionable insights for cyberattack prevention.
- Ensure security measures are in place as defenses.
- Regularly meet requirements and standards of cybersecurity testing.
Challenges of Web Application Security Testing
We understand web application security testing is critical to ensuring usability, functionality, and security. However, application security testing often comes with problems. For instance, software developers face obstacles in their testing efforts. The most common challenges that often developers face in web application security testing are as follows:
Diverse Web Technologies
Regular Changes
Applications require regular changes and updates with the evolving industry. This requires adding new features and fixing bugs and security vulnerabilities. This continuous cycle often leads to new vulnerabilities, resulting in regular application security testing.
Third-Party Integrations
Data Protection and Breach
Three Main Approaches to Application Security Testing
To obtain accurate test results, there are three main approaches to security testing. The following approaches are used at different frequencies, and they provide proper answers to security testing.
Automated Scans
Automated Scans + Manual Testing
Application Penetration Tests
Automated Scans: Pros and Cons
Pros
- Automated penetration testing can identify vulnerabilities faster than manual penetration testing.
- With automated penetration testing, many applications can be tested to secure web applications.
- Automated penetration testing offers consistency in the approach and reduces the risk of human error.
- It is one of the most cost-effective solutions for web application security testing.
Cons
- Automated penetration testing follows a predefined set of steps as it has been programmed to test. Hence, the scope is limited.
- Automated penetration testing can usually generate a high number of false positives and false negatives. Flagging non-existing complexities wastes the time and resources of the security teams.
- Similar to AI, the generic nature of these automated penetration tests lacks attention to detail.
- Automated penetration testing primarily focuses on complexities and may overlook human-centric threats like phishing and hacking.
Risks of Relying Solely on Automated Scans?
Automated scans offer all the right advantages, like being less time-consuming and cost-effective. However, relying solely on automated scans leads to a false sense of security and leaves critical vulnerabilities unaddressed. This happens because automated scans follow a predefined pattern and instructions to identify vulnerabilities. With no human insight, potential issues are overlooked.
Further, automated tools cannot replicate manual techniques like human psychology, social engineering, and others. The validations performed by automated scanners cannot identify technical vulnerabilities such as authentication bypasses, access control weaknesses, and more. Such vulnerabilities have potential risks and can lead to serious consequences and potential cyberattacks.
For instance, a company that uses only automated scans often fails to identify zero-day vulnerabilities. This can exploit the application and lead to a data breach, where customers’ sensitive information can be stolen before any further action can be taken if there is an e-commerce platform with a complex interaction. Automated scans often fail to detect complex flaws, which can lead to exploiting transaction records and financial losses.
Risk-Based Approach to Prioritization
The risk-based approach to prioritization simply helps you assess which testing method is required for which application. This approach depends on various factors, such as data sensitivity, third-party integrations, new amendments, assessment performance, size, and more.
After assessing these factors, you can opt for an automated scan or a manual test for your application. This way, you can test your application effectively and efficiently. A risk-based approach is effective, but regular manual penetration tests are as important as automated scans.
What is Manual Penetration Testing & its Necessity?
Necessity of Manual Penetration Testing
Manual Penetration Tests: Pros and Cons
Pros
- Manual penetration testing can stimulate real hacker behavior.
- With manual penetration testing, there is no chance of finding false positives.
- This approach offers a comprehensive report on all vulnerabilities.
- Think out of the box and can reveal unexpected application vulnerabilities.
Cons
- Testing all systems can be cost-prohibitive and time-consuming
- Manual penetration testing requires high-level specialists, which leads to higher costs.
- Results can vary from specialist to specialist.
- There is a chance of human errors and omissions, leaving many application vulnerabilities intact.
When to Prioritize Manual Penetration Testing
Now, the question comes when to prioritize manual penetration. Or which application should undergo manual testing or the frequency of manual tests? With the fast-evolving cyber world, testing your applications at least once a year is necessary, according to the experts. This way, you can stay ahead of the latest technology and security measures you might have to take. Besides this, there are other times when manual penetration should be prioritized.
Every application requires major system changes after a certain time. Hence, manual penetration is necessary when you launch new features or networks in your application. With manual penetration testing, you can ensure no vulnerabilities or security flaws before the launch of new features.
Combining Automated and Manual Testing for Optimal Security
A manual testing method can validate automated scans and lower your application’s risk ratings. Further, it is important to note that manual testing doesn’t improve the depth of the analysis, but it is more reliable for securing critical risks.
Case Studies: When to Use Each Method
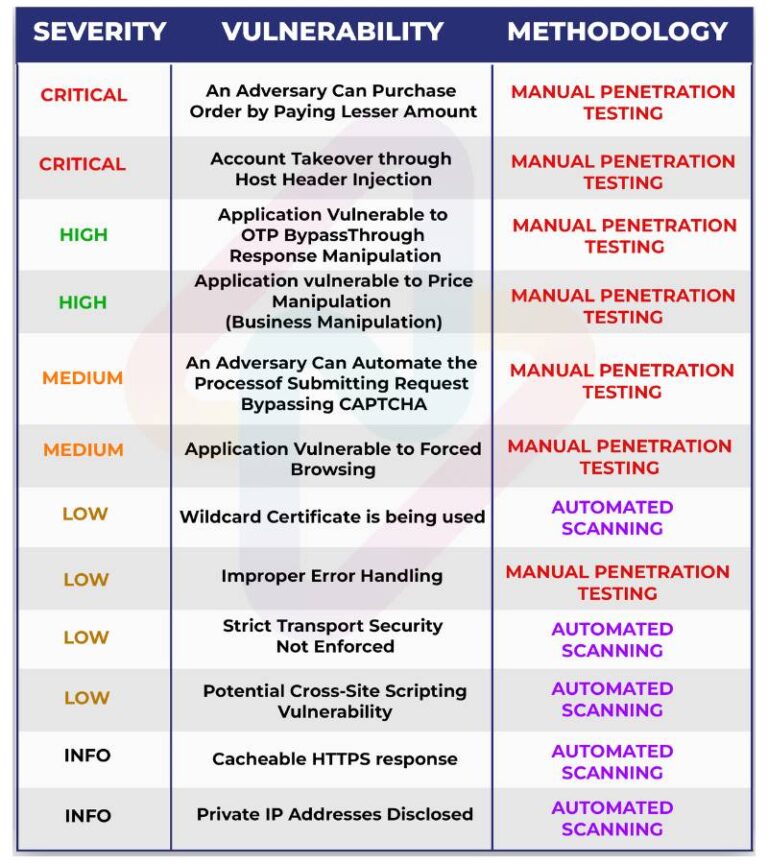
Case Study 1: E-Commerce Platform
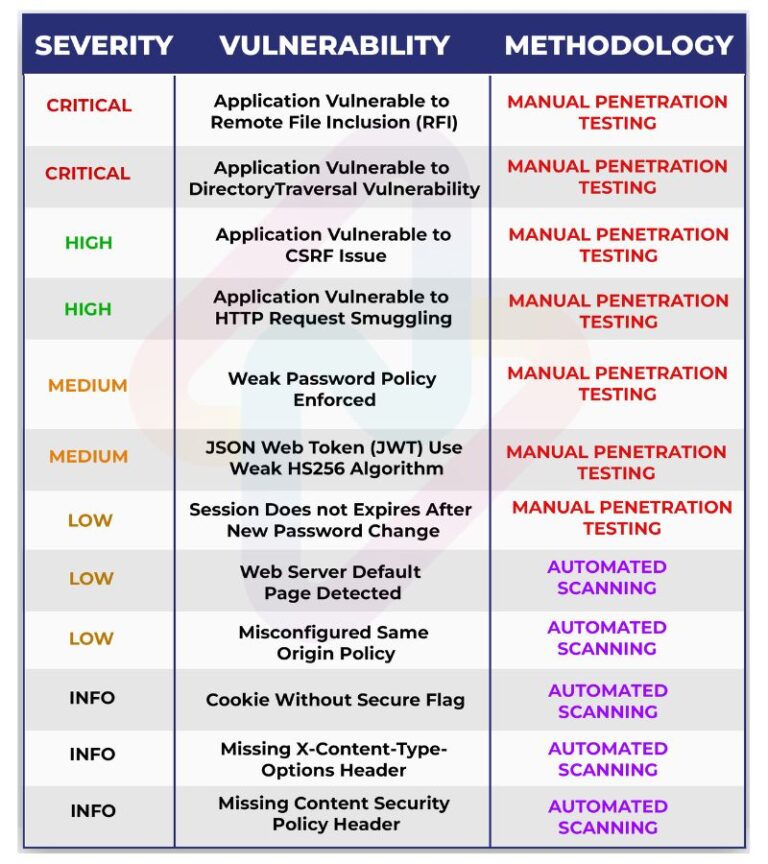
Case Study 2: Fintech Application
How Peneto Labs Can Help?
Peneto Labs can help you examine your ongoing security levels through various security audits. We recognize the limitations of automated testing in a holistic security approach through which you can assess the potential risks and address them before getting exploited.
So, sign up and consult with our experts to get penetration testing for web apps on a budget for you and your organization!
Ready to secure your web apps with the best penetration testing approach? Whether you’re leaning towards automated testing for speed and efficiency or manual testing for thorough, expert analysis, Peneto Labs has you covered. Our team of certified professionals is here to help you choose the right solution tailored to your needs. Contact us today to schedule a consultation and take the first step towards fortifying your digital defenses.
Contact Penetolabs now and secure your web apps with confidence!
WhatsApp us
